CloakShield

CloakShield - Node to node communications - is a onion-routing implementation for CloakCoin's network traffic.
CloakShield provides secure communications between nodes on the Cloak network using symmetric RSA encryption backed by an Elliptic Curve Diffie Hellman key exchange (ECDH). This allows nodes to exchange data securely, providing protection from snoopers (man in the middle) and imposters (sybil attack). CloakShield is designed to secure both ENIGMA and decentralized CloakCoin applications, and will ensure your data stays as private as possible. CloakShield allows the encrypted sending of data to one or more recipients. When sending to a single recipient, the payload is RSA encrypted using the ECDH shared secret. When sending to multiple recipients, the payload is encrypted using a one-time key and the key is then encrypted for each recipient using the ECDH/RSA method
Generating a shared Encryption Key
In order for Alice and Bob to communicate securely, they must agree on a shared encryption key. CloakShield uses ECDH to accomplish this:
- Alice has ENIGMA private key dA and ENIGMA public key QA=dAG (where Gis the generator for the elliptic-curve). Bob has ENIGMA private key dB and ENIGMA public key QB=dBG.
- Alice has Bob’s ENIGMA public key dB from the ENIGMA announcements he sends to the network to announce his availability for cloaking assistance. She uses her private key dA and Bob’s public key QB to calculate shared secret dAQB=dAdBG
(ECDH_compute_key in OpenSSL). - Alice then creates a SHA256 hash of the secret and passes the hash to the
OpenSSLEVP_BytesToKeymethod in order to derive an encryption key and IV, which will be used to encrypt data for Bob (using symmetric RSA encryption). - Alice is now able to create CloakShield secured messages for Bob. When Bob receives a Cloak Shielded message from Alice, he reads Alice’s public key from the message header and generates the same shared secret key as Alice, as per the steps above (with his secret key, instead of Alice’s). The Cloak wallet maintains a list of active CloakShield keys and will check the list for an existing CloakShield key before generating one.
CloakShield Data
CloakShield allows any Cloak data objects to be serialized and transmitted securely to one or more recipients. A CloakShield data packet-header contains the sender’s ENIGMA public key and the public keys hashes of the recipients. CloakShield headers contain a verification hash, which is generated using the sender’s public key and the raw unencrypted data. This hash is verified during decryption of CloakShield data to ensure that the recipient info in the header matches the encryption key, and that the data has not been altered.
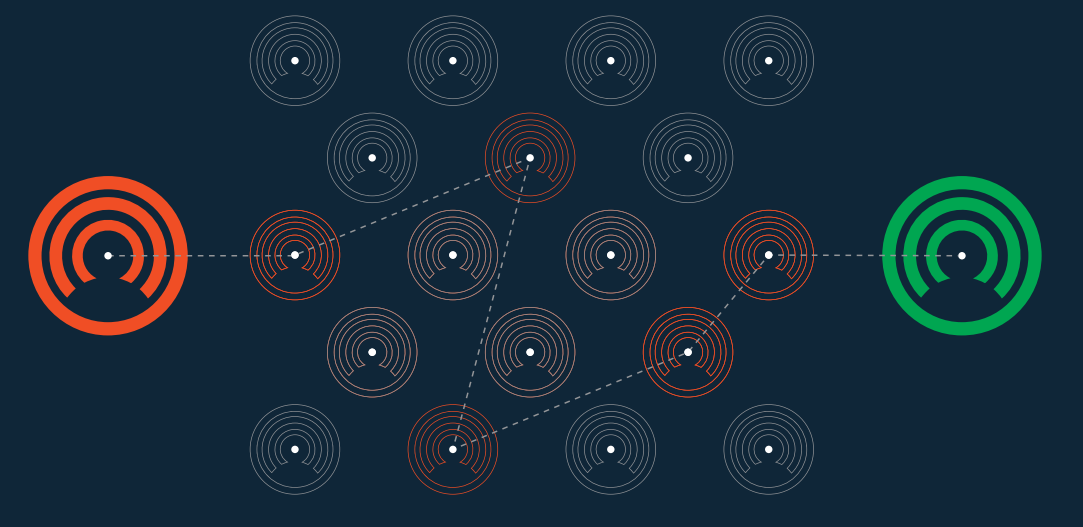
CloakShield Onion Routing
Onion routing is a technique (used by TOR) for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which “peels” away a single layer, uncovering the data’s next destination. When the final layer is decrypted, the message arrives at its destination. The sender remains anonymous because each intermediary knows only the location of the immediately preceding and following nodes.
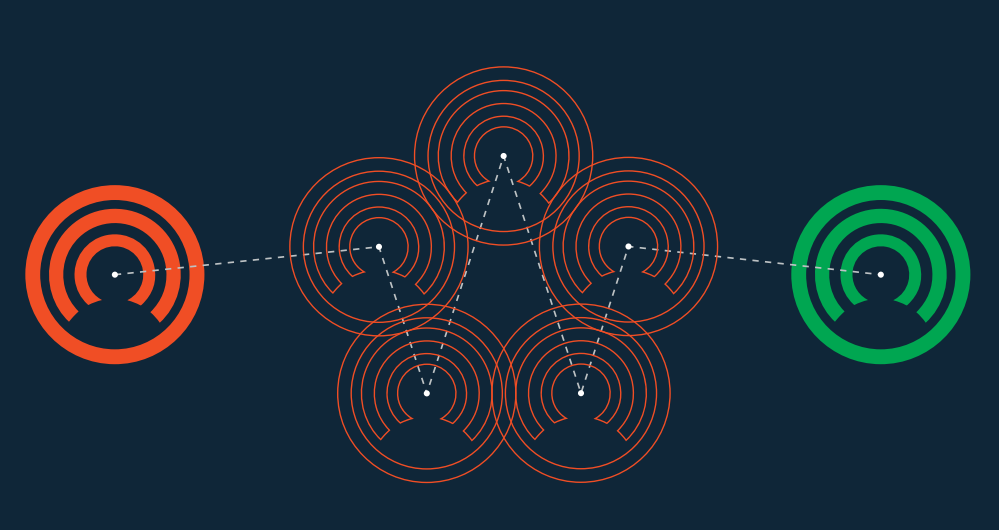
Onion Routing Analogy
The addition of ‘onion routing’ functionality to the ENIGMA network (using CloakShield) allows nodes to communicate indirectly to circumvent traffic analysis. This hampers attempts at determining which nodes are communicating with each other or which nodes submitting transactions to the CloakCoin network. When an ENIGMA node wishes to communicate with another ENIGMA node it selects a number of other ENIGMA nodes to act as relays for the communication. Each encrypted layer can only be decrypted by the intended relay [for which the specific layer was encrypted]. After decrypting a layer, the relay passes the data to the next relay node. This routing continues it until the data reaches its intended recipient and all layers have been decrypted in turn by the selected relay nodes. Due to the self-contained nature of the ENIGMA network, exit nodes are not required and CloakShield ensures there is no risk of a relay node reading or altering the encrypted data.
CloakShield - Node to Node Communications
Cloak uses the ENIGMA system to faclilate private/secure transactions through stealth addresses.
On startup, each Cloak wallet generates a [NID_secp256k1] keypair (Cloaking Encryption Key/CEK) to enable them to derive ad-hoc secrets using ECDH with their private key and the recipient's public key. This communication forms the basis on all node-to-node communications relating to ENIGMA. This ECDH based encrypted communication is also utilized for onion-routed data, which is handled by CloakShield. CloakShield utilizes end-to-end encryption and delivers secure communication, allowing nodes to circumvent traffic analysis.
When onion routing is enabled, the client will attempt to construct a valid onion route for the data using the list of ENIGMA peers that it is aware of. The node may not have a direct connection to the ENIGMA peers, but that is not necessary as CloakData (data packed for routing with CloakShield) packets are relayed peer-to-peer. An onion route will typically consist of 3 distinct routes to the destination node, with 3 node hops per route. Multiple routes are used to cope with situations where a routing node drops offline.
Nodes periodically send out an ENIGMA Announcement to peers to advertise their services for onion routing. Other nodes on the network store the announcements (until they expire or are replaced with an update) and use them to construct the onion routes.
Combined with ENIGMA, it is designed for privacy, utilizing up to 25 hops using symmetric RSA encryption backed by an ECDH key exchange. This means all network traffic in a ENIGMA transaction is impossible to monitor or trace.
CloakShield Onion Routing
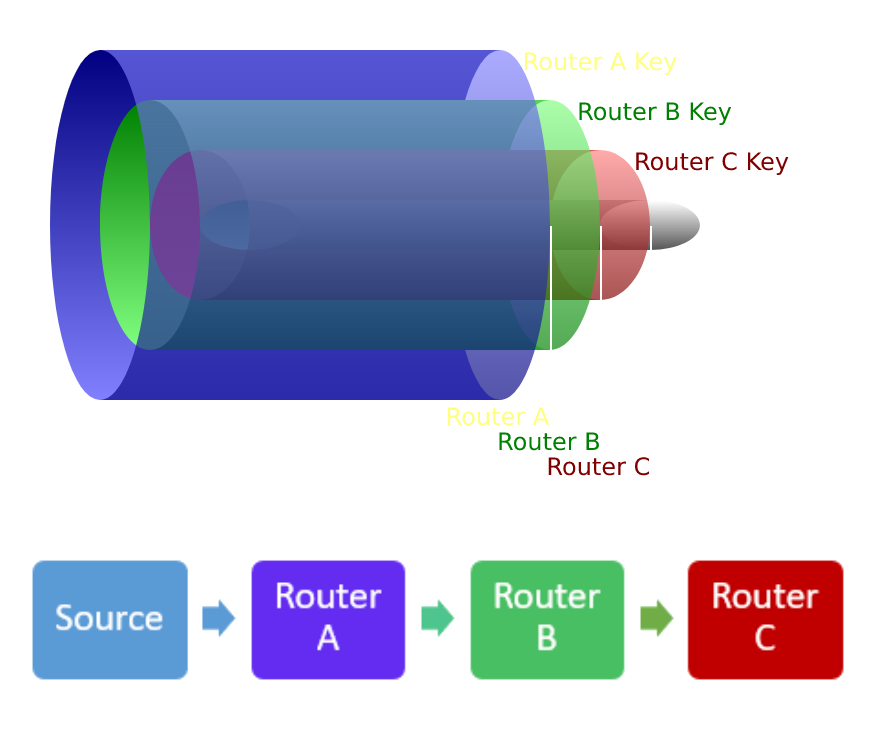
✅ Uses end-to-end encryption and provides secure communication.
✅ Designed to secure both ENIGMA and decentralized CloakCoin applications, and will ensure your data stays as private as possible. ✅ Allows the encrypted sending of data to one or more recipients. ✅ Allows any CloakCoin data objects to be serialized and transmitted securely to one or more recipients. ✅ Allows nodes to communicate indirectly to circumvent traffic analysis. ✅ Provides an onion routing network with up to 25 hops
