ENIGMA

The inspiration for the name ENIGMA comes from the meaning of the original Greek word – riddle, puzzle, mystery – and describes Cloakcoin's ENIGMA: Private, Secure, Untraceable and Decentralized Transactions.
ENIGMA in cooperation with CloakShield makes it impossible for outside observers to trace any transaction done with CloakCoin.
ENIGMA - Technical Transaction Process
When a node sends funds via ENIGMA to an stealth address, the following happens:
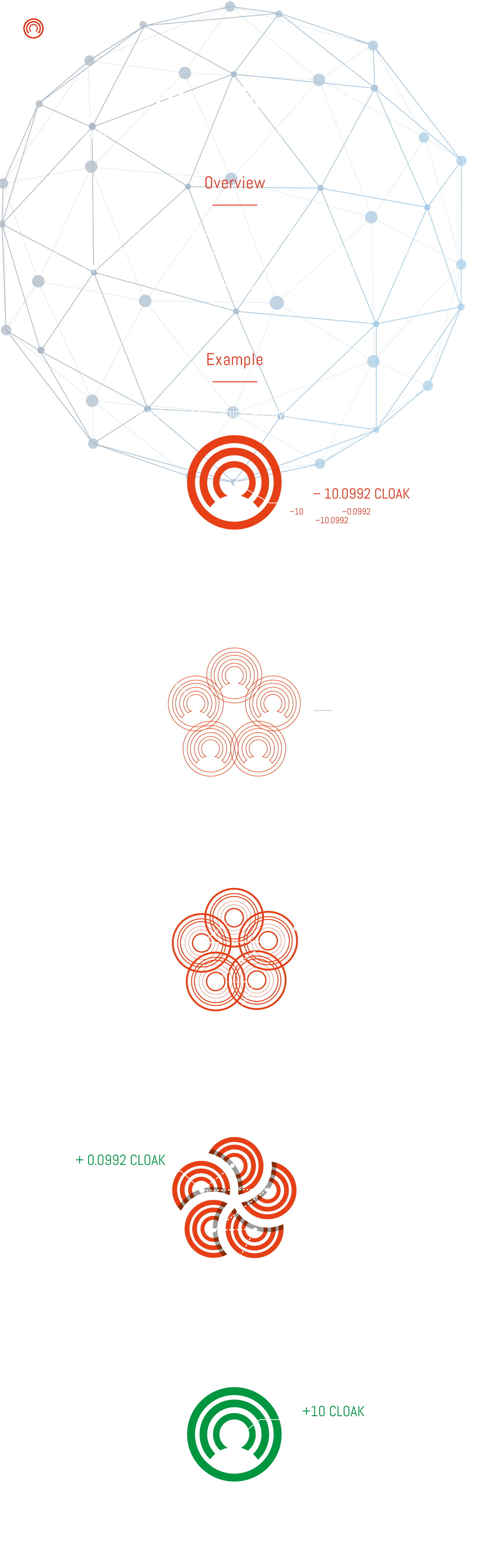
- Sender generates inputs to cover amount sent, ENIGMA reward and network fee (1% at 0 coins thru 0.2% at 1000 and higher coins).
- Sender generates a CloakingRequest object (containing unique stealth nonce for this request).
- Sender generates between 2 to 4 one-time stealth payment addresses using the recipients stealth address and splits the sent amount randomly between the addresses.
- Sender decides how many participants are going to be used. From 5-25 participants can be chosen (each participant gets 80-120% of an equally split ENIGMA fee).
- Sender onion routes CloakRequest to network. The request contains the send amount so that Cloakers know how much to reserve.
- Cloaker picks up CloakRequest and decides to participate.
- Cloaker supplies x inputs to sender and a stealth address and stealth hash (for their change).
- Cloaker sends CloakingAcceptResponse to Sender. This contains stealth address, stealth nonce and TX inputs.
- Sender waits until enough Cloakers have accepted.
- Sender creates ENIGMA transaction using own inputs and Cloaker inputs. Inputs are shuffled.
- Sender creates TX ouputs for all Cloakers. The outputs randomly split their change and return it to them. This also allocates the cloaking reward to Cloakers.
- Sender creates their own change returns for the ENIGMA TX. These are one-time stealth payment addresses.
- The sender calculates the network TX fee and subtracts this from their own change return.
- The sender sends the ENIGMA TX to the Cloakers for signing.
- Cloakers check the TX to ensure their inputs are present and correct and that there are one-time payment addresses linked to one of their stealth addresses with payment that exceeds the input amount.
- Cloakers sign or reject the TX and send signatures to sender.
- Sender collates the signatures and transmits the finalized, signed TX to the network.
- Nodes scan incoming transactions for stealth payments and ENIGMA payments and detect any payments or change. Keypairs and addresses are generated for any matching payments and generated keys/addresses are saved to the local wallet.
ENIGMA - Transaction Process





How are stealth and Enigma transactions detected/received?
All incoming transactions are scanned. Stealth transactions are scanned for first (using the default ephemeral pubkey contained in a random OP_RETURN TX output). After this, ENIGMA transactions are then scanned for. ENIGMA transactions also use the standard ephemeral pubkey, but payments use an additional step involving a further derived key. ENIGMA outputs are generated using a hash of the ephemeral pubkey, a private stealth address hash and the output index.
When scanning for ENIGMA transactions, the zero-index payment addresses are generated for each owned stealth address [HASH(ephemeral_pubkey, hash_stealth_secret, 0)]. If a match is found for the zero-index of a stealth address, additional addresses are generated for the remaining indexes [num_tx_outputs] and these are scanned against to detect payments. See FindEnigmaTransactions in wallet.cpp for more info.
A similar scanning method is employed by Cloakers prior to signing an ENIGMA TX to ensure they are getting reimbursed correctly. See GetEnigmaOutputsAmounts in wallet.cpp for more info.
ENIGMA Transaction
It’s no secret that central banks print money whenever the mood strikes. And, they always get away with it. Why? Because they hold absolute power over the flow of cash and there’s no one to stop them.
As a fully transparent crypto project, it’s our duty to keep the community well informed. Yes, we’re a privacy coin. But no, CloakCoin is not a faceless organization lacking accountability.
CloakCoin’s ENIGMA transactions are untraceable and anonymous, but our money supply is just the opposite. Crypto projects operating under the guise of privacy, with no transparency, are little different than gov’t printing presses. With a fully auditable monetary supply, CloakCoin cements its dedication to community transparency while serving as a digital equivalent to cash. You can find on every ENIGMA transaction in the block explorer, the inputs on the top and the outputs on the bottom. The number depends on how many 'Cloakers' were used. If for example, 21 Cloakers/mixers are used, there will be 21 matching outputs and also 21 times as many inputs. Only the sender and recipient know who the real sender is. So, in essence, 20 other people pretended to also send coins but really sent them back to themselves.
ENIGMA Challenge
 After much internal tweaking, revising and testing, Team Cloak announced on 8th May 2019 the CloakCoin ENIGMA Competition! If someone cracks the mentioned ENIGMA transaction, the person will be rewarded with an amount of 10,000 CLOAK!
After much internal tweaking, revising and testing, Team Cloak announced on 8th May 2019 the CloakCoin ENIGMA Competition! If someone cracks the mentioned ENIGMA transaction, the person will be rewarded with an amount of 10,000 CLOAK!
How many CLOAK's has been sent❓ Who is the Sender❓ Who is the Receiver❓
CloakCoin ENIGMA Whitepaper

Since 2014, Cloak has been working towards making financial privacy simple and accessible to almost everyone. Our decentralized payment system — ENIGMA — ensures complete transactional anonymity.
The whitepaper, details the evolution of CloakCoin! The technology is thoroughly explained that means that CloakCoin is prepared to become one of the true innovators in the crypto world.
CloakCoin ENIGMA Audio Book
 If you’re strapped for time, you can listen on the go to the audio version of the CloakCoin ENIGMA Whitepaper!
If you’re strapped for time, you can listen on the go to the audio version of the CloakCoin ENIGMA Whitepaper!